Blockchain technology represents a revolutionary approach to data management, functioning as a decentralized, distributed ledger that records transactions across a network of computers. This structure ensures transparency, immutability, and resistance to tampering, making it foundational for applications like cryptocurrencies, supply chain tracking, and decentralized finance (DeFi).
However, as blockchain adoption grows, so does the sophistication of threats targeting these networks. Security is paramount because vulnerabilities can result in massive financial losses, data breaches, and erosion of user trust, as seen in high-profile incidents like the DAO hack or various exchange breaches. This article delves into the core elements that bolster blockchain security, examines common types of attacks, and discusses mitigation strategies to safeguard these systems.
What Makes a Blockchain Network Secure
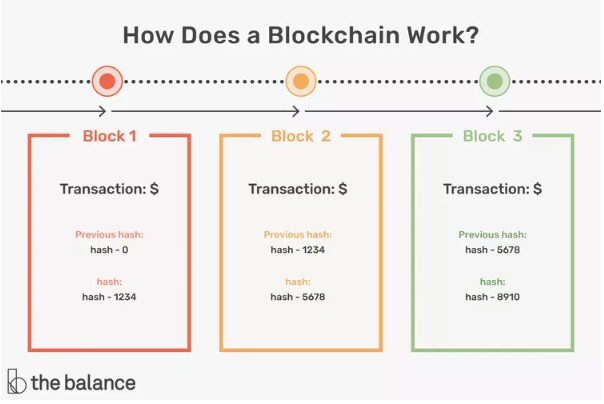
Blockchain's security stems from a combination of architectural and cryptographic principles designed to prevent unauthorized alterations and ensure reliable operation. These features work synergistically to create a robust ecosystem resistant to many traditional cyber threats.
Immutability: Once data is added to the blockchain, it becomes nearly impossible to alter without consensus from the network. This is achieved through cryptographic linking of blocks, where each block contains a hash of the previous one. Any attempt to change a block would require recalculating all subsequent hashes, a process that demands enormous computational power on large networks.
Cryptographic Hash Functions: These algorithms transform input data into fixed-length strings, serving as digital fingerprints. Algorithms like SHA-256 ensure data integrity; even minor changes in the input produce vastly different hashes, alerting the network to tampering. (1)
Consensus Mechanisms: These protocols govern how nodes agree on the validity of transactions and blocks, preventing fraudulent activities.
Easy visualization of
- Proof of Work (PoW): Miners compete to solve complex mathematical puzzles, adding blocks to the chain. This mechanism deters attacks by requiring significant energy and hardware investment, as seen in Bitcoin's network. (2)
- Proof of Stake (PoS): Validators are selected based on the amount of cryptocurrency they stake as collateral. This energy-efficient alternative reduces centralization risks but incorporates penalties for malicious behavior. (3)
Decentralization: By distributing control across numerous nodes worldwide, blockchain eliminates single points of failure. No central authority means an attacker must compromise a majority of the network to exert influence, which is prohibitively expensive on mature blockchains.
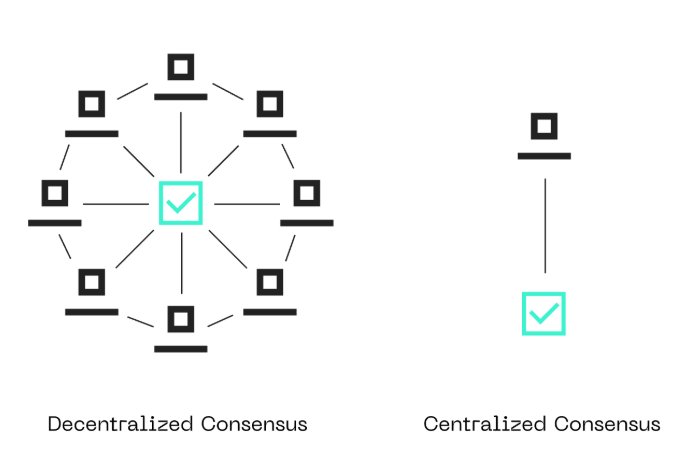
Timestamping: Transactions are timestamped and recorded immutably, providing a verifiable chronology that supports applications requiring proof of existence or order, such as legal documents or intellectual property claims.
Resistance to Double Spending: Through consensus, the network verifies that assets are not spent more than once. This is enforced by requiring majority agreement, making it costly for attackers to forge transactions without controlling the network.
Types of Attacks on Blockchain Networks
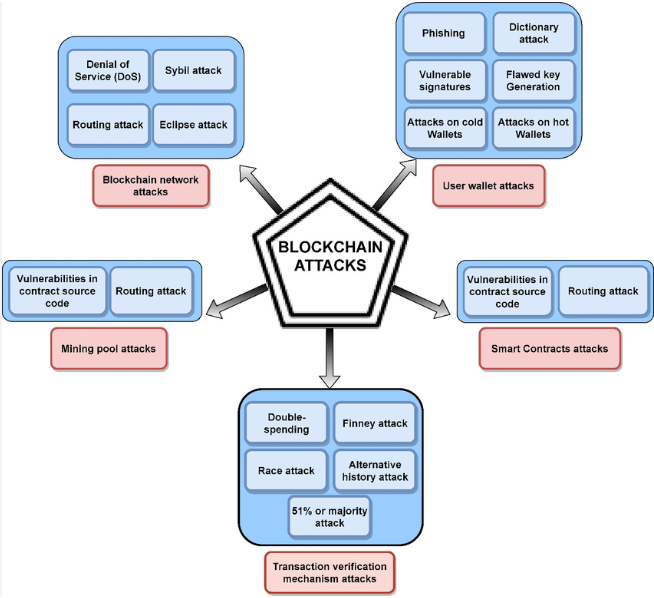
Despite its strengths, blockchain is not impervious to attacks. Threats can target various layers, from the underlying protocol to user interfaces, exploiting weaknesses in design, implementation, or human behavior.
Consensus/Protocol Layer Attacks:
- 51% Attack: An attacker gains control of over 50% of the network's computational power (in PoW) or stake (in PoS), allowing them to reverse transactions, double-spend, or censor blocks. This has affected smaller networks like Bitcoin Gold but is less feasible on giants like Bitcoin due to high costs.
- Selfish Mining: Miners secretly mine on a private chain fork and release it strategically to invalidate the public chain, gaining disproportionate rewards and potentially destabilizing the network.
- Finney Attack: A form of double-spending where an attacker pre-mines a block containing a transaction, spends the same funds elsewhere, and then releases the pre-mined block to reverse the second spend.
- Race Attack: Involves broadcasting two conflicting transactions simultaneously, tricking a recipient into accepting one while the network confirms the other, leading to double-spending.
- Long Range Attack: Attackers create an alternate chain from a distant point in history, inserting fraudulent transactions, often exploiting PoS vulnerabilities where staking old coins is cheap. (4)
Network Layer Attacks:
- Sybil Attack: An attacker creates multiple fake identities to flood the network, potentially isolating nodes or influencing voting in consensus.
- Eclipse Attack: By monopolizing a node's peer connections, an attacker isolates it from the true network, feeding false blockchain data to enable double-spends or other manipulations.
- Timejacking Attack: Manipulates a node's internal clock by sending false timestamps, potentially slowing block propagation or enabling other attacks like double-spending.
- Denial of Service (DoS): Overwhelms nodes with excessive traffic, causing crashes or delays in transaction processing. (5)
Data Layer Attacks:
- Transaction Replay Attack: Valid transactions from one chain are replayed on a forked chain, leading to unintended fund transfers post-hard fork.
- Transaction Malleability: Alters transaction IDs without invalidating signatures, potentially disrupting confirmations and enabling fraud.
- Cryptographic Attacks: Exploits weak keys or quantum computing threats to crack encryption, though current blockchains use quantum-resistant algorithms in some cases. (6)
Application Layer Attacks:
- Smart Contract Vulnerabilities: Coding errors, like reentrancy bugs, allow attackers to drain funds, as in the infamous DAO exploit on Ethereum.
- Rug Pull: Developers promote a project, attract investments, then abruptly withdraw liquidity, causing the token's value to plummet.
- Phishing and User-Level Breaches: Social engineering tricks users into revealing private keys via fake websites or emails, leading to wallet drains, as occurred in the Mt. Gox incident. (7)
Mitigation Strategies and Best Practices
To counter these threats, blockchain developers and users must adopt proactive measures. Enhancing decentralization through diverse node participation reduces the risk of 51% attacks. Requiring multiple confirmations before accepting transactions mitigates double-spending variants like race or Finney attacks. Robust encryption, regular code audits, and incorporating randomness in protocols help against cryptographic and network attacks. For Sybil and Eclipse threats, implement IP rate limiting, increase peer connections, and conduct penetration testing. Smart contracts should undergo third-party audits, and users must be educated on phishing via multi-factor authentication and hardware wallets. Ongoing monitoring and protocol upgrades, such as Ethereum's shift to PoS, further strengthen defenses.
Blockchain's inherent strengths of immutability, decentralization, and consensus help provide a solid foundation for security, yet evolving threats like 51% attacks and smart contract exploits demand constant vigilance. As the technology matures, advancements in quantum-resistant cryptography and hybrid consensus models promise enhanced resilience. Stakeholders must prioritize audits, education, and community-driven improvements to maintain trust and integrity in blockchain ecosystems.
References
- The Ultimate Guide to Blockchain Security
- Deep Dive into Blockchain Security: Vulnerabilities and Protective Measures
- The Importance of Blockchain Security and How to Prevent Threats Before They Strike
- Common Blockchain Network Attacks and Vulnerabilities
- Blockchain Attack Vectors: Risks & Impact
- Types of Blockchain Attacks You Should Know
- Common Blockchain Security Vulnerabilities
About Netcoins
Established in 2014 in Vancouver, British Columbia, Netcoins is a registered Restricted Dealer with the provincial securities commissions and a registered Money Services Business (MSB) with FINTRAC. The platform operates under BIGG Digital Assets Inc., a publicly traded company listed on the TSX Venture Exchange (TSXV: BIGG), and complies with applicable public company regulatory requirements.
The information provided in the blog posts on this platform is for educational purposes only. It is not intended to be financial advice or a recommendation to buy, sell, or hold any cryptocurrency. Always do your own research and consult with a professional financial advisor before making any investment decisions. Cryptocurrency investments carry a high degree of risk, including the risk of total loss. The blog posts on this platform are not investment advice and do not guarantee any returns. Any action you take based on the information on our platform is strictly at your own risk. The content of our blog posts reflects the authors’ opinions based on their personal experiences and research. However, the rapidly changing and volatile nature of the cryptocurrency market means that the information and opinions presented may quickly become outdated or irrelevant. Always verify the current state of the market before making any decisions.



.png)

.jpg)
.png)




